Identify a True Statement About a Vulnerability Scanner
Add Advanced Support for access to phone community and chat support 24 hours a day. Nessus Professional will help automate the vulnerability scanning process save time in your compliance cycles and allow you to engage your IT team.

The Ultimate Guide To Ot Vulnerability Management Verve Industrial
Log4j-scanner is a project derived from other members of the open-source community by CISAs Rapid Action Force team to help organizations identify potentially vulnerable web services affected by.

. The results for this scanner are thus approximate. Exact name of registrant as specified in its charter Delaware. Research Apr 04 2022.
The use of this information to identify and track you online is known as device or browser fingerprinting. Cambridge Massachusetts 02140 617 655-6580. The sum total of these outputs can be used to render a unique fingerprint for tracking and.
Although this is a server-level vulnerability different. Detector Summary Asset scan settings Compliance standards. The API_KEY_SCANNER detector identifies vulnerabilities related to API keys used in your cloud deployment.
API key vulnerability findings. An issue with a server header sent with every HTTP response would be reported on every page on the site rather than. This could create many vulnerabilities when the fix was a single file or configuration change.
As browsers become increasingly entwined with the operating system many unique details and preferences can be exposed through your browser. Research Apr 04 2022. In GitLab 1312 and earlier all DAST vulnerabilities found in a scan were listed individually for each URL the vulnerability was found on.
Hi All Can someone please give me a mitigation for 97861 - Network Time Protocol NTP Mode 6 Scanner Vulnerability for WS-C3750G-24TS-1U Model Switch with IOS - 12255SE10 Thanks Prasanna Kumar Desireddy. Due to the large number of findings from the truffleHog3 scanner w entropy we were only able to review a selection of these findings. Since it is tough to figure out where this vulnerability is present it might be safer to assume the project is vulnerable and patching the library is the best action to remove the risk from code execution.
To evaluate the quality of the scanners we manually reviewed the findings from each scanner classifying each as secret a true positive or not a false positive. Vulnerability severity levels CVE ID requests Policies Scan execution policies Scan result policies Security scanner integration Secure and Protect Terminology Deploy and release your application Environments and deployments Environments Dashboard Protected environments Deployment safety Deployment approvals Roll out an application incrementally Deploy to AWS Deploy to. Nessus is the most comprehensive vulnerability scanner on the market today.
Buy a multi-year license and save. The next step is to identify all projects using the Log4J library. Probing the activities of cloud-based cryptocurrency-mining groups and Lapsus back from vacation Expert Perspective Apr 01.
Cyber Threats This Week in Security News - April 1 2022. To resolve this limit API key. Theyre also now used in Burp Suites core scanner.
There are API keys being used too broadly. Employer Identification No 100 Cambridgepark Drive. An estimated 15005000 patients in a persistent vegetative state are now living in Germany This condition is defined as one without any clinical evidence for psychologically interpretable contact between the patient and the outside world despite phases of wakefulness in which the patients eyes are open The treatment of vegetative patients is a major.
Heartbleed could be exploited regardless of whether the vulnerable OpenSSL instance is running as a TLS server or client. 81-1591163 State or other jurisdiction of incorporation or organization I. Heartbleed was a security bug in the OpenSSL cryptography library which is a widely used implementation of the Transport Layer Security TLS protocol.
If exploited the vulnerability could allow malicious actors to gain root privilege escalation. It was introduced into the software in 2012 and publicly disclosed in April 2014. These requests can be adapted to target arbitrary discrepancies in header parsing and theyre used to automatically identify request smuggling vulnerabilities by HTTP Request Smuggler - an open source Burp Suite extension developed to help with such attacks.
The project might be vulnerable if versions between 20-beta9 and 2141 are used. THE SECURITIES ACT OF 1933.

Top 10 Vulnerability Scanners Most Popular Scanners In 2022

Risk Assessment Vs Vulnerability Assessment How To Use Both Bmc Software Blogs

Vulnerability Management Life Cycle Npcr Cdc

Announcing Remote Scanning For Tanium Comply Identify Vulnerabilities On Any Connected Device Tanium

Container Vulnerability Scanning For Cloud Native Applications

Introduction To Vulnerability Management Bmc Software Blogs
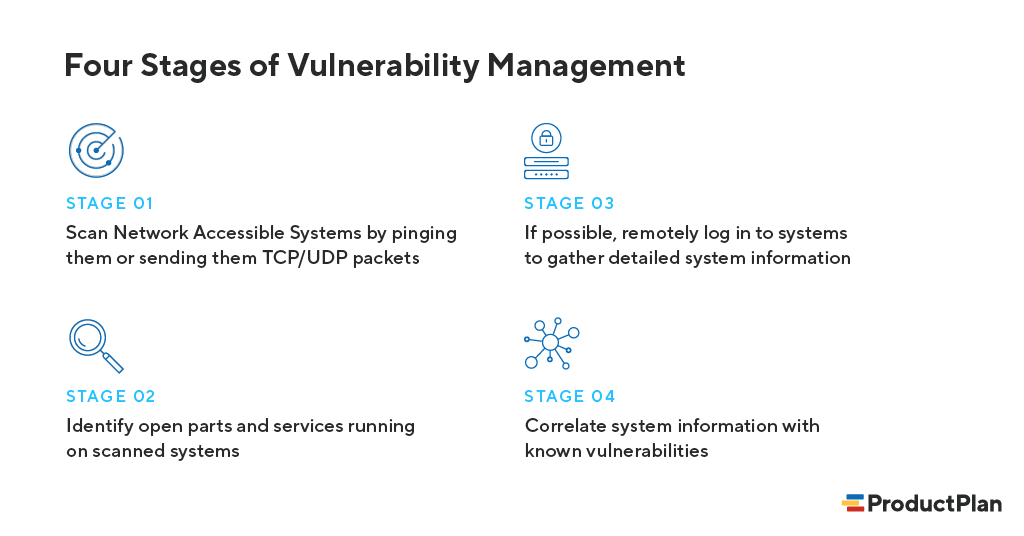
What Is Product Vulnerability Definition And Overview
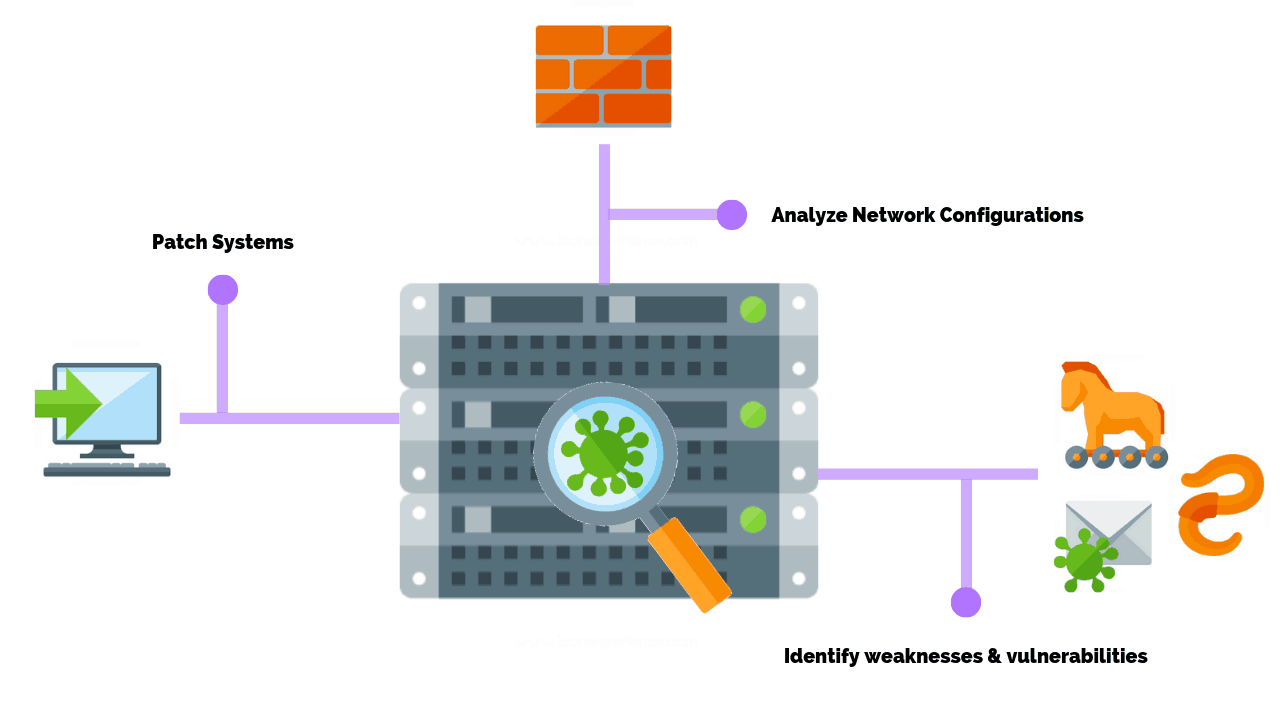
How Often Should You Perform A Network Vulnerability Scan

Network Vulnerability Assessment And Management Guide

Announcing Remote Scanning For Tanium Comply Identify Vulnerabilities On Any Connected Device Tanium

Pin On Cyber Security For Small Business

Pin By The Project Artist On Understanding Psychology Understanding Psychology Psychology Understanding

Cloud Vulnerability Scanning Vulnerability F Secure Cloud Services
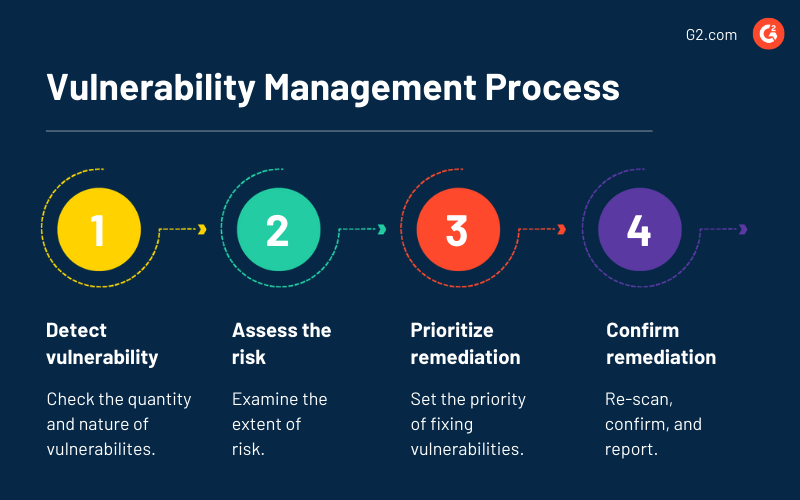
What Is Vulnerability Management Get The Answers You Need

Top 10 Vulnerability Scanners Most Popular Scanners In 2022
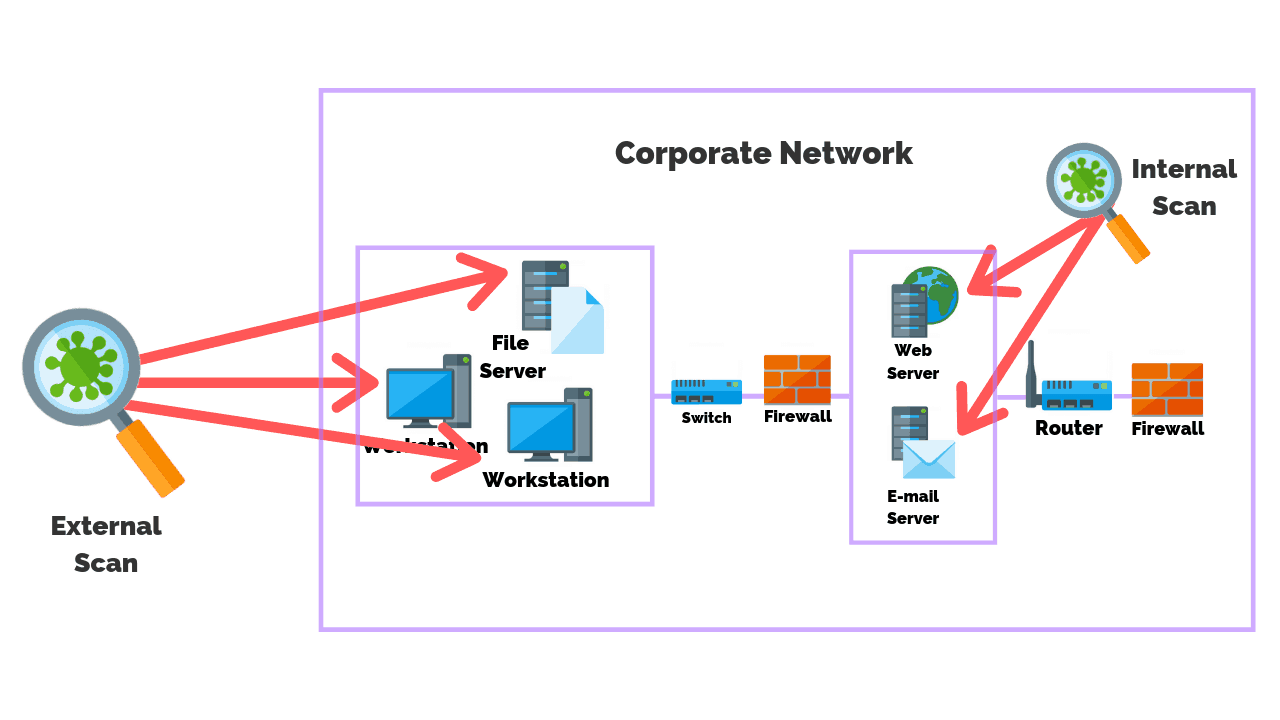
Internal Vs External Vulnerability Scans What S The Main Difference

Top 10 Vulnerability Scanners Most Popular Scanners In 2022

Vulnerability Scanner What Is It And How Does It Work Snyk
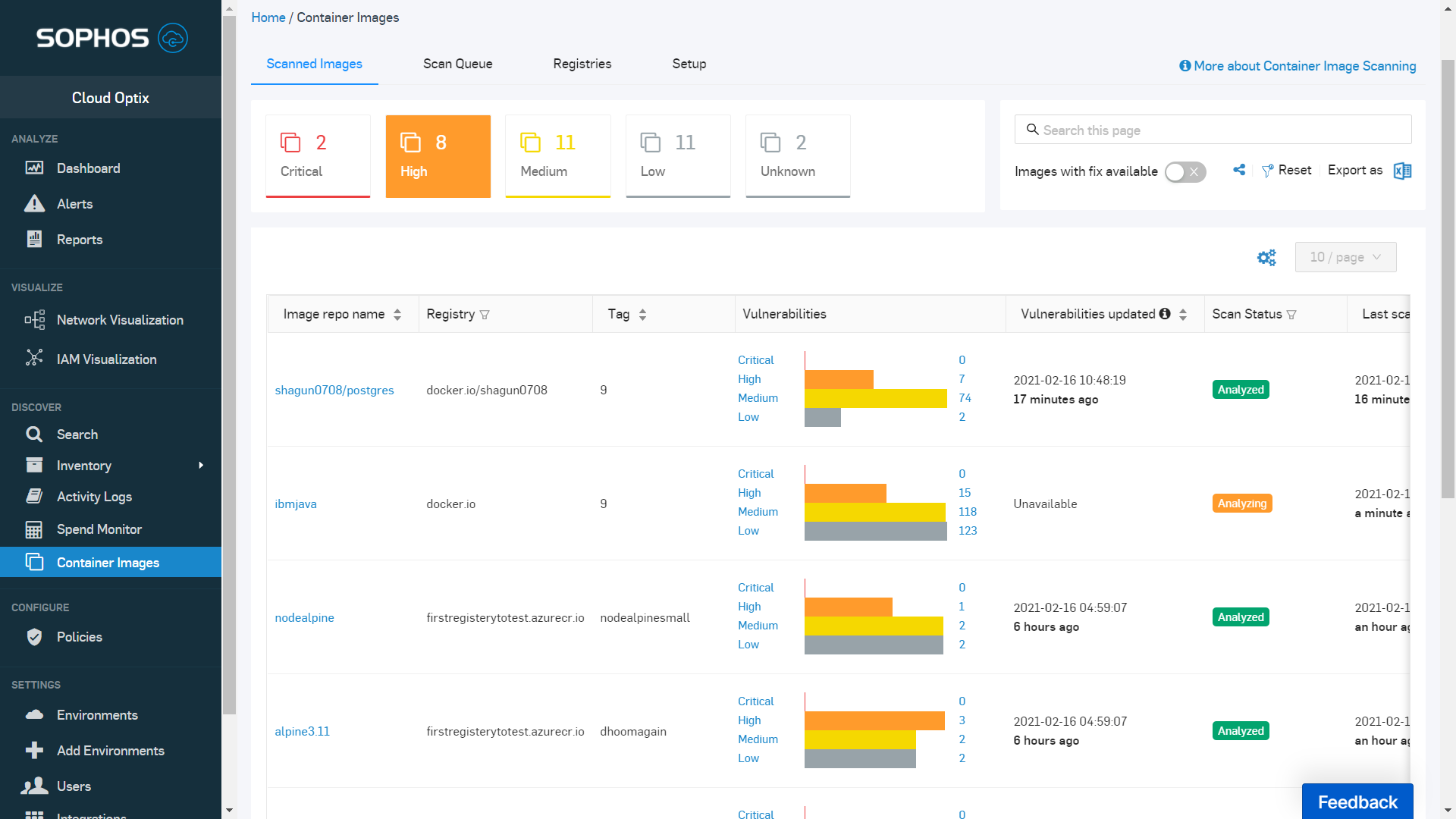
Introducing Container Vulnerability Scanning From Sophos Sophos News
Comments
Post a Comment